#Latest browsing code
Explore tagged Tumblr posts
Text
One way to spot patterns is to show AI models millions of labelled examples. This method requires humans to painstakingly label all this data so they can be analysed by computers. Without them, the algorithms that underpin self-driving cars or facial recognition remain blind. They cannot learn patterns.
The algorithms built in this way now augment or stand in for human judgement in areas as varied as medicine, criminal justice, social welfare and mortgage and loan decisions. Generative AI, the latest iteration of AI software, can create words, code and images. This has transformed them into creative assistants, helping teachers, financial advisers, lawyers, artists and programmers to co-create original works.
To build AI, Silicon Valley’s most illustrious companies are fighting over the limited talent of computer scientists in their backyard, paying hundreds of thousands of dollars to a newly minted Ph.D. But to train and deploy them using real-world data, these same companies have turned to the likes of Sama, and their veritable armies of low-wage workers with basic digital literacy, but no stable employment.
Sama isn’t the only service of its kind globally. Start-ups such as Scale AI, Appen, Hive Micro, iMerit and Mighty AI (now owned by Uber), and more traditional IT companies such as Accenture and Wipro are all part of this growing industry estimated to be worth $17bn by 2030.
Because of the sheer volume of data that AI companies need to be labelled, most start-ups outsource their services to lower-income countries where hundreds of workers like Ian and Benja are paid to sift and interpret data that trains AI systems.
Displaced Syrian doctors train medical software that helps diagnose prostate cancer in Britain. Out-of-work college graduates in recession-hit Venezuela categorize fashion products for e-commerce sites. Impoverished women in Kolkata’s Metiabruz, a poor Muslim neighbourhood, have labelled voice clips for Amazon’s Echo speaker. Their work couches a badly kept secret about so-called artificial intelligence systems – that the technology does not ‘learn’ independently, and it needs humans, millions of them, to power it. Data workers are the invaluable human links in the global AI supply chain.
This workforce is largely fragmented, and made up of the most precarious workers in society: disadvantaged youth, women with dependents, minorities, migrants and refugees. The stated goal of AI companies and the outsourcers they work with is to include these communities in the digital revolution, giving them stable and ethical employment despite their precarity. Yet, as I came to discover, data workers are as precarious as factory workers, their labour is largely ghost work and they remain an undervalued bedrock of the AI industry.
As this community emerges from the shadows, journalists and academics are beginning to understand how these globally dispersed workers impact our daily lives: the wildly popular content generated by AI chatbots like ChatGPT, the content we scroll through on TikTok, Instagram and YouTube, the items we browse when shopping online, the vehicles we drive, even the food we eat, it’s all sorted, labelled and categorized with the help of data workers.
Milagros Miceli, an Argentinian researcher based in Berlin, studies the ethnography of data work in the developing world. When she started out, she couldn’t find anything about the lived experience of AI labourers, nothing about who these people actually were and what their work was like. ‘As a sociologist, I felt it was a big gap,’ she says. ‘There are few who are putting a face to those people: who are they and how do they do their jobs, what do their work practices involve? And what are the labour conditions that they are subject to?’
Miceli was right – it was hard to find a company that would allow me access to its data labourers with minimal interference. Secrecy is often written into their contracts in the form of non-disclosure agreements that forbid direct contact with clients and public disclosure of clients’ names. This is usually imposed by clients rather than the outsourcing companies. For instance, Facebook-owner Meta, who is a client of Sama, asks workers to sign a non-disclosure agreement. Often, workers may not even know who their client is, what type of algorithmic system they are working on, or what their counterparts in other parts of the world are paid for the same job.
The arrangements of a company like Sama – low wages, secrecy, extraction of labour from vulnerable communities – is veered towards inequality. After all, this is ultimately affordable labour. Providing employment to minorities and slum youth may be empowering and uplifting to a point, but these workers are also comparatively inexpensive, with almost no relative bargaining power, leverage or resources to rebel.
Even the objective of data-labelling work felt extractive: it trains AI systems, which will eventually replace the very humans doing the training. But of the dozens of workers I spoke to over the course of two years, not one was aware of the implications of training their replacements, that they were being paid to hasten their own obsolescence.
— Madhumita Murgia, Code Dependent: Living in the Shadow of AI
71 notes
·
View notes
Text
Alright, time for some obscure Persona 3 history. I was browsing the old Japanese Persona 3 website, when I stumbled across something interesting. This is what it looks like normally (Vanilla P3 specifically)

But on certain captures of this website on the Wayback Machine, it was set to midnight (JST). The website was coded to have a special easter egg that goes off around that time, as the Dark Hour clock appears...

And then the site is now in the Dark Hour.
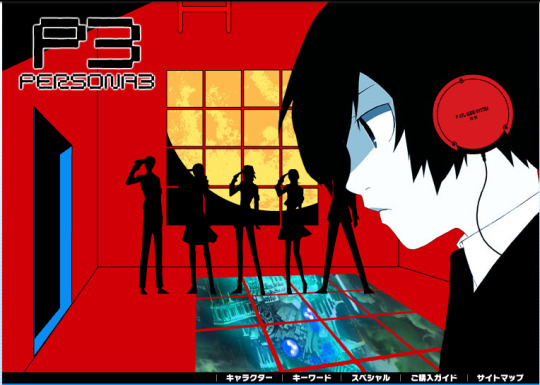
Click on the Akihiko, Mitsuru, Fuuka, and Junpei, and cause them to disappear, and Yukari will start to glow.

And you will have unlocked a secret section of the Japanese website! This mostly contained diary entries on various perspectives regarding the Dark Hour (on one section, there even was text regarding Strega's revenge request site), but there also were some secret downloads, namely a supposedly early version of a Persona 3 commercial (which Google translate says it was rejected by a TV station for containing subliminal content?), MP3 downloads, a video showcasing the P3 girls in maid costumes in Tartarus, and a message from Elizabeth to the player (which acted as a tease towards the new Elizabeth requests being added in FES). I have the latest capture of the secret section of the website, as well as a capture of the website during the Dark Hour so you can try this for yourself! (You'll need Ruffle for this)

Speaking of the Persona 3 website, let's go over some of the evolution of the P3 website! Here's the original version of the website when Persona 3 was first announced.
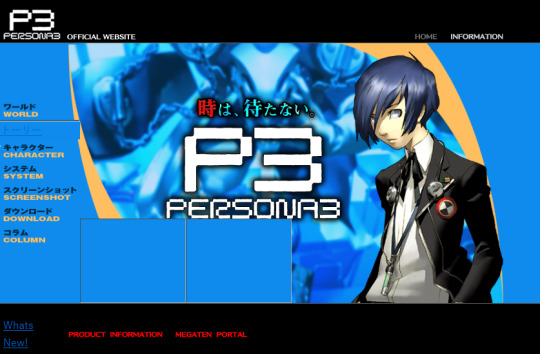
It was updated from P3's initial announcement in March towards May when the newer website was launched, last major update was Fuuka Yamagishi's character profile. Here's a Wayback Machine link for you to try it out yourself.
Here is the website around the time they were teasing FES. Makoto is replaced with Aigis, and there was a section containing audio messages from the developers that would help tease FES. (So far, they are lost media? Hopefully some fan manages to recover them)
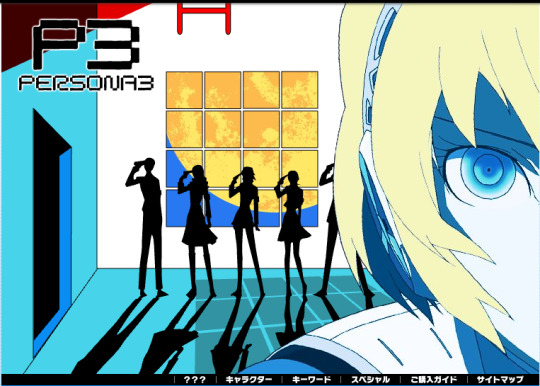
And here is the FES version of the website, with both the normal and Dark Hour variations. (Metis replaces Yukari on the Dark Hour variation of the website, though I cannot access the secret section, probably because the silly toaster is blocking the way)


And just for funzies, I thought I'd include this link regarding P3 ads in this blogpost on the old AtlusNet. Hopefully somebody will get high quality scans of the magazine ads and promos used to promote P3 in both Japanese and English.
Now to wonder, what other crazy P3 promotional stunts did Atlus do? I know there was a countdown on the Atlus USA website that counted down the days until the release information on FES would be provided to the world, and I'm well aware of various Japanese gaming magazines that had various info on P3 (that so far only exist as JPEGS on the old Digital Devil Database and other websites), but man, I wanna know more. The fans should be archiving a lot of this stuff. Reload has re-triggered my Persona 3 phase, and I want to know more secrets about the game. I honestly think there's a lot of cool things waiting for us down the line...
#persona 3#atlus#2000s game advertising was wild man#hopefully a lot of this doesn't end up as lost media#i'm just doing my best to archive a lot of this stuff for future fans of persona 3#maybe if atlus had the guts they'd bring back the old websites for april fools day#course i'm waiting for someone to remake the old persona 3 website but this time with the reload art for the characters
192 notes
·
View notes
Text
Librera Reader is a highly customizable and feature-rich application for reading e-books in PDF, EPUB, MOBI, DjVu, FB2, TXT, RTF, AZW, AZW3, HTML, CBZ, CBR, DOC, DOCX, formats.
With its intuitive, yet powerful, interface, Librera makes ebook reading a veritable pleasure. It even features a unique auto-scrolling, hands-free Musician's mode, with controllable speed.
F-Droid version is based on the latest MuPDF and support Android 4.1+.
The only difference between Librera FD (F-Droid) and Librera PRO is the absence of Google Play services and Google Drive book synchronization in Librera FD.
Just a few Librera main features:
Easy document discovery by configurable criteria:
Auto-Scan (user-specified folders)
Browse folders (using an in-app file explorer)
Recent (featuring a reading-progress indicator)
Support for bookmarks, annotations, and EPUB3 tables of contents
Configurable Day and Night modes
Configurable link color (hence, footnotes and endnotes color)
Support for many popular offline dictionaries
Vertical-scroll lock
Auto- and manual centering of documents
Custom ad-hoc CSS coding
Single-page view of two-page documents
Musician's mode with configurable scroll speed
Customizable TTS reading and built-in media player
Page-wise TTS recording to MP3 or WAV
Multi-word text search
Support for archived (.zip) documents
Support for RTL languages (Thai, Hebrew, Arabic, etc.)
Import and export of settings, auto-backup of current session
Leading initials in FB2 documents
RSVP reading (à la Spritz)
Movable bookmarks, w/ a floating indicator
And a whole bunch of other features for you to check out.
You can read books in your web browser with the Librera Book Reader https://librera.mobi/online-book-reader/
The best way to fully appreciate Librera Reader, however, is to use our restriction-free Librera PRO version from Google Play.
If you enjoy Librera, please consider making a donation: https://www.patreon.com/librera
8 notes
·
View notes
Note
On one hand, having a group chat of some sort to discuss hero-ing shenanigans seems useful. On the other, using Discord or even a text group chat seems like a pretty good way for some tech company to get their hands on a whole bunch of secret identities. Do superheroes have a proprietary app for this sort of thing? Or do they have another solution?
For the JLA and Titans-related heroes, Cyborg's hacking powers render this a total non-issue. On the client end, they use the same texting and messaging apps as everyone else, with a few added bits and bobbles of interface.
On the server end, software that Cyborg set up (took him about 5 minutes) casually intercepts every message they send before it reaches any servers corporations could extract data from, redirects to a private, secure instance of the same chat/texting software (getting Facebook's total source code without authorization is about 0.02 seconds of effort for him), also redirects anyone else in the same chatspace to the same private server, then filters all the messages for sensitive info (there's ways people can flag their own messages) before hacking back into the corporate servers to re-insert a record of some messages they would expect to see as if their own servers had handled everything, so even if admins try to investigate they won't be able to tell who's using the pirated chat instance to ban them.
It's all very complicated from a human perspective but it's all happening totally automatically in real time so it doesn't really matter. The end result is the Titans just have a regular old Discord server that, as far as Discord the company is concerned, doesn't exist, but they can still invite people to who are using regular Discord accounts or chat from their accounts on other normal servers, and other apps are all similarly seamless and convenient.
The Avengers have basically an ultra-high-end spy version of Signal (the app, not Batman's latest son). At first they were just using SHIELD messaging software but after not too long Stark made his own. But the way it's set up, not even Stark has access to all the messages that are sent to anyone besides him. During Civil War he tried to shut down the whole service so the other side couldn't use it, and failed. He just made it too secure and autonymous. Unless someone has the app open and is currently looking at what he wants to see, not even Cyborg could extract chatlogs from it.
The X-Men, X-Force, and X-Factor are basically left out in the cold and forced to use a combination of regular services (some encrypted like Signal) and, when available, and only for the people who agree to it, telepathic chatrooms.
Whoever is "hosting" a telepathic chatroom isn't consciously aware of the messages being subconsciously relayed in real time, but, there's nothing to stop them browsing if they get curious, and as soon as they need to focus and use their powers on anything else strenuous or with stakes, the whole thing shuts down. But the chatlogs being stored in the literal memories of the people in them, that only prevents new messages from being sent for a while (and from being able to literally visually see it), and if the telepathic chatrooms need a new "host" to run it, little is lost in the hand-off.
Of course all of that is just about text chat. Earpiece comms are fairly standard among superheroes, so a lot of communication happens over comms voice calls/recorded voice messages, and that's its own whole topic.
#BronzeRealms#superheroes on Discord#superhero texting#marvel#dc comics#marvel comics#dc universe#justice league#jla#dc titans#the avengers#marvel avengers#x men#dc cyborg#telepathy#the Kimmunicator is worth mentioning but I'll just leave it down here in tags since only a handful of heroes have one#x force#x factor#discord chat
4 notes
·
View notes
Text
✨ A little about us - Freshly Updated! ✨
Hey everyone,
Time for an update on our ever-evolving pinned post! We've grown and changed since our last intro, so here's the latest on who we are now. 🌟
👩💻 Meet the Crew!
Chloe (she/her): The cornerstone of our group. At 24 years old, I'm a transfem French computer science enthusiast, deeply immersed in the world of computer imagery and vision. My passion lies in exploring rendering engines, classifying images, and detecting those cleverly disguised fake images.
Sarah (she/they): Our cherished first tulpa, with a bigender (nb/f) identity. Sarah has a scholarly aura and a heart of gold. She's continuously evolving, bringing so much joy and sweetness into our lives.
Lucy (she/her): Our tech wizard and gaming aficionado. Lucy combines a tomboyish flair with her love for coding and gaming, adding a dynamic and playful energy to our collective spirit.
Mel Summer (they/he): The serene, genderfluid (mostly masc) soul among us. Mel enjoys a laid-back existence, often content to observe and reflect quietly. Their presence is like a soothing undercurrent, subtly enriching our shared experience.
🌈 Our Space
Our blog is a tapestry of our varied interests and experiences – a place where no single theme rules. It's a vibrant mix of fascinating finds and personal glimpses. 🎨 Fun Facts
We navigate the world with aphantasia, unable to visualize images mentally. It's a distinct perspective that shapes our experiences in unique ways.
We're collectively enamored with @madladypercent – she's absolutely charming!
We're in the midst of developing a game centered on speedrunning, coding, and TAS. Stay tuned for our devlogs as this exciting project unfolds! (Project paused for now)
⚠️ DNI (Do Not Interact) if you are:
Under 18
Sysmedicalist
Transmedicalist
TERF
SWERF
Tankie
Tradcon
Right-winger
🔞 Content Warning
Just a heads-up: I occasionally reblog content for those 18 and older, so please exercise discretion while browsing. 💌 Let's Connect!
We're all about building connections and sharing our collective journey. Feel free to send us messages, reblog our posts, or simply enjoy a stroll through our eclectic digital world.
Stay awesome and keep shining! ✨
--
Chloe, Sarah, Lucy, and Mel Summer
8 notes
·
View notes
Text
@vigilant-cleric sent
"Hello, Babette. I've heard you were given some free literature recently. Please allow me to complete it with this copy of 'Tenets of the Helmite faith' and the reminder that the temple is open for spiritual guidance today."

𝙻𝙴𝚃𝚃𝙴𝚁𝚂 . unprompted interactions ────────────────────────
Oh wow, did Ashen also read smut romance novels ? Or maybe he was the smut peddler in disguise. A subtle, cheeky smile as knowing eyes flick towards the offered book, a glance over its title. What a strange name for such flavor of literature, the young woman thinks to herself.

❝ Spiritual guidance sounds magical. ❞ Probably a code word for the secret book club these helmites have going on. No wonder they have to hide it — They would only earn weird looks if people got wind of the church coming together for reviewing the latest spicy literature.
But the book really didn't look like one of said caliber. That thing was heavy, eyes idly browsed through its contents as pale fingers flicked through the sites. A rule-book of some sorts. Ashen surely had a strange taste. The hexblood wasn't one to kinkshame.
❝ I will join the temple later, then. Maybe we can discuss the . . . book you gave me. ❞
#vigilant-cleric#It took me so long but i tell you i cried a little when I got father Ashen in my inbox#He straight up gave her a bible and wants her to speak her sins#You have to love Ashen...#✂ ˚ The Hexed Seamstress ˚⠀⠀/ ic .#✂ ˚ I take commissions ˚⠀⠀/ answered .#✂ ˚ Knitting something nice :) ˚⠀⠀/ q .
2 notes
·
View notes
Text
Prezenta - The AI-Powered Presentation Architect HTML Landing Page Template
Prezenta, the AI-Powered HTML template, offers a modern design, responsive layout, and RTL support. It’s SEO-optimized with accessible and interactive features for a superior user experience.
Live Demo Buy Now
Overview:
Step into the future of presentations with Prezenta, the AI-Powered Presentation Architect HTML Landing Page Template. Designed to transform your ideas into visually stunning and interactive experiences, Prezenta is the epitome of innovation in web design. With its clean and modern design, this template offers a canvas that makes your content stand out in the most sophisticated way possible. It’s not just about looks; Prezenta is responsive across all devices, ensuring your audience enjoys a flawless experience whether on desktop, tablet, or mobile.
Prezenta understands the global market, offering RTL language support for scripts like Arabic and Hebrew, making it an inclusive solution for diverse audiences. The template’s adaptability extends to its light and dark themes, catering to user preferences and different lighting environments. Behind the scenes, Prezenta is fortified with W3C validated HTML and CSS, guaranteeing maximum compatibility and top-notch performance across all major web browsers. It’s built on the latest technologies and coding standards, promising regular updates and ongoing support to keep your presentations at the cutting edge.
Dive into a world of possibilities with comprehensive documentation that guides you through easy customization, allowing you to tailor your landing page to perfection. Prezenta’s accessible design ensures that it’s a landing page for everyone, including users with disabilities. It’s not just user-friendly; it’s also optimized for search engines, ensuring your content gets the visibility it deserves. With fast loading times, Prezenta respects your audience’s time, providing an efficient browsing experience.
Social media integration means your landing page can achieve increased fame with just a click. Customize to your heart’s content with SCSS files, and captivate your audience with interactive animations and effects. Prezenta doesn’t just present content; it enhances it with advanced features for an unparalleled user experience. Add visual flair with icon and badge libraries, and build trust with testimonial and review sections. Showcasing your content is a breeze with customizable sliders and carousels, and navigation is made effortless with a back-to-top button. Lastly, stay connected with your audience through a PHP contact form. Prezenta is more than a template; it’s a comprehensive landing page that empowers you to create, share, and succeed.
Live Demo Buy Now
2 notes
·
View notes
Text
If you live in Russia, there’s no avoiding Yandex. The tech giant—often referred to as “Russia’s Google”—is part of daily life for millions of people. It dominates online search, ride-hailing, and music streaming, while its maps, payment, email, and scores of other services are popular. But as with all tech giants, there’s a downside of Yandex being everywhere: It can gobble up huge amounts of data.
In January, Yandex suffered the unthinkable. It became the latest in a short list of high-profile firms to have its source code leaked. An anonymous user of the hacking site BreachForums publicly shared a downloadable 45-gigabyte cache of Yandex’s code. The trove, which is said to have come from a disgruntled employee, doesn’t include any user data but provides an unparalleled view into the operation of its apps and services. Yandex’s search engine, maps, AI voice assistant, taxi service, email app, and cloud services were all laid bare.
The leak also included code from two of Yandex’s key systems: its web analytics service, which captures details about how people browse, and its powerful behavioral analytics tool, which helps run its ad service that makes millions of dollars. This kind of advertising system underpins much of the modern web’s economy, with Google, Facebook, and thousands of advertisers relying on similar technologies. But the systems are largely black holes.
Now, an in-depth analysis of the source code belonging to these two services, by Kaileigh McCrea, a privacy engineer at cybersecurity firm Confiant, is shedding light on how the systems work. Yandex’s technologies collect huge volumes of data about people, and this can be used to reveal their interests when it is “matched and analyzed” with all of the information the company holds, Confiant’s findings say.
McCrea says the Yandex code shows how the company creates household profiles for people who live together and predicts people's specific interests. From a privacy perspective, she says, what she found is “deeply unsettling.” “There are a lot of creepy layers to this onion,” she says. The findings also reveal that Yandex has one technology in place to share some limited information with Rostelecom, the Russian-government-backed telecoms company.
Yandex’s chief privacy officer, Ivan Cherevko, in detailed written answers to WIRED’s questions, says the “fragments of code” are outdated, are different from the versions currently used, and that some of the source code was “never actually used” in its operations. “Yandex uses user data only to create new services and improve existing ones,” and it “never sells user data or discloses data to third parties without user consent,” he says.
However, the analysis comes as Russia’s tech giant is going through significant changes. Following Russia’s full-scale invasion of Ukraine in February 2022, Yandex is splitting its parent company, based in the Netherlands, from its Russian operations. Analysts believe the move could see Yandex in Russia become more closely connected to the Kremlin, with data being put at risk.
“They have been trying to maintain this image of a more independent and Western-oriented company that from time to time protested some repressive laws and orders, helping attract foreign investments and business deals,” says Natalia Krapiva, tech-legal counsel at digital rights nonprofit Access Now. “But in practice, Yandex has been losing its independence and caving in to the Russian government demands. The future of the company is uncertain, but it’s likely that the Russia-based part of the company will lose the remaining shreds of independence.”
Data Harvesting
The Yandex leak is huge. The 45 GB of source code covers almost all of Yandex’s major services, offering a glimpse into the work of its thousands of software engineers. The code appears to date from around July 2022, according to timestamps included within the data, and it mostly uses popular programming languages. It is written in English and Russian, but also includes racist slurs. (When it was leaked in January, Yandex said this was “deeply offensive and completely unacceptable,” and it detailed some ways that parts of the code broke its own company policies.)
McCrea manually inspected two parts of the code: Yandex Metrica and Crypta. Metrica is the firm’s equivalent of Google Analytics, software that places code on participating websites and in apps, through AppMetrica, that can track visitors, including down to every mouse movement. Last year, AppMetrica, which is embedded in more than 40,000 apps in 50 countries, caused national security concerns with US lawmakers after the Financial Times reported the scale of data it was sending back to Russia.
This data, McCrea says, is pulled into Crypta. The tool analyzes people’s online behavior to ultimately show them ads for things they’re interested in. More than 300 “factors” are analyzed, according to the company’s website, and machine learning algorithms group people based on their interests. “Every app or service that Yandex has, which is supposed to be over 90, is funneling data into Crypta for these advertising segments in one form or another,” McCrea says.
Some data collected by Yandex is handed over when people use its services, such as sharing their location to show where they are on a map. Other information is gathered automatically. Broadly, the company can gather information about someone’s device, location, search history, home location, work location, music listening and movie viewing history, email data, and more.
The source code shows AppMetrica collecting data on people’s precise location, including their altitude, direction, and the speed they may be traveling. McCrea questions how useful this is for advertising. It also grabs the names of the Wi-Fi networks people are connecting to. This is fed into Crypta, with the Wi-Fi network name being linked to a person’s overall Yandex ID, the researcher says. At times, its systems attempt to link multiple different IDs together.
“The amount of data that Yandex has through the Metrica is so huge, it's just impossible to even imagine it,” says Grigory Bakunov, a former Yandex engineer and deputy CTO who left the company in 2019. “It's enough to build any grouping, or segmentation of the audience.” The segments created by Crypta appear to be highly specific and show how powerful data about our online lives is when it is aggregated. There are advertising segments for people who use Yandex’s Alice smart speaker, “film lovers” can be grouped by their favorite genre, there are laptop users, people who “searched Radisson on maps,” and mobile gamers who show a long-term interest.
McCrea says some categories stand out more than others. She says a “smokers” segment appears to track people who purchase smoking-related items, like e-cigarettes. While “summer residents” may indicate people who have holiday homes and uses location data to determine this. There is also a “travelers” section that can use location data to track whether they have traveled from their normal location to another—it includes international and domestic fields. One part of the code looked to pull data from the Mail app and included fields about “boarding passes” and “hotels.”
Some of this information “doesn’t sound that unusual” for online advertising, McCrea says. But the big question for her is whether creating personalized adverting is a good enough reason to collect “this invasive level of information.” Behavioral advertising has long followed people around the web, with companies hoovering up people’s data in creepy ways. Regulators have failed to get a grip on the issue, while others have suggested it should be banned. “When you think about what else you could do, if you can make that kind of calculation, it's kind of creepy, especially in Russia,” McCrea says. She suggests it is not implausible to create segments for military-aged men who are looking to leave Russia.
Yandex’s Cherevko says that grouping users by interests is an “industry standard practice” and that it isn’t possible for advertisers to identify specific people. Cherevko says the collection of information allows people to be shown specific ads: “gardening products to a segment of users who are interested in summer houses and car equipment to those who visit gas stations.” Crypta analyzes a person’s online behavior, Cherevko says, and “calculates the probability” they belong to a specific group.
“For Crypta, each user is represented as a set of identifiers, and the system cannot associate them with a natural person in the real world,” Cherevko claims. “This kind of set is probabilistic only.” He adds that Crypta doesn’t have access to people’s emails and says the Mail data in the code about boarding passes and hotels was an “experiment.” Crypta “received only de-identified information about the category from Mail,” and the method has not been used since 2019, Cherevko says. He adds that Yandex deletes “user geolocation” collected by AppMetrica after 14 days.
While the leaked source code offers a detailed view of how Yandex’s systems may operate, it is not the full picture. Artur Hachuyan, a data scientist and AI researcher in Russia who started his own firm doing analytics similar to Crypta, says he did not find any pretrained machine learning models when he inspected the code or references to data sources or external databases of Yandex’s partners. It’s also not clear, for instance, which parts of the code were not used.
McCrea’s analysis says Yandex assigns people household IDs. Details in the code, the researcher says, include the number of people in a household, the gender of people, and if they are any elderly people or children. People’s location data is used to group them into households, and they can be included if their IP addresses have “intersected,” Cherevko says. The groupings are used for advertising, he says. “If we assume that there are elderly people in the household, then we can invite advertisers to show them residential complexes with an accessible environment.”
The code also shows how Yandex can combine data from multiple services. McCrea says in one complex process, an adult’s search data may be pulled from the Yandex search tool, AppMetrica, and the company’s taxi app to predict whether they have children in their household. Some of the code categorizes whether children may be over or under 13. (Yandex’s Cherevko says people can order taxis with children’s seats, which is a sign they may be “interested in specific content that might be interesting for someone with a child.”)
One element within the Crypta code indicates just how all of this data can be pulled together. A user interface exists that acts as a profile about someone: It shows marital status, their predicted income, whether they have children, and three interests—which include broad topics such as appliances, food, clothes, and rest. Cherevko says this is an “internal Yandex tool” where employees can see how Crypta’s algorithms classify them, and they can only access their own information. “We have not encountered any incidents related to access abuse,” he says.
Government Influence
Yandex is going through a breakup. In November 2022, the company’s Netherlands-based parent organization, Yandex NV, announced it will separate itself from the Russian business, following Russia’s invasion of Ukraine. Internationally, the company, which will change its name, is planning to develop self-driving technologies and cloud computing, while divesting itself from search, advertising, and other services in Russia. Various Russian businessmen have been linked to the potential sale. (At the end of July, Yandex NV said it plans to propose its restructuring to shareholders later this year.)
While the uncoupling is being worked out, Russia has been trying to consolidate its control of the internet and increasing censorship. A slew of new laws requires more companies and government services in the country to use home-grown tech. For instance, this week, Finland and Norway’s data regulators blocked Yandex’s international taxi app from sending data back to Russia due to a new law, which comes into force in September, that will allow the Federal Security Service (FSB) access to taxi data.
These nationalization efforts coupled with the planned ownership change at Yandex are creating concerns that the Kremlin may soon be able to use data gathered by the company. Stanislav Shakirov, the CTO of Russian digital rights group Roskomsvoboda and founder of tech development organization Privacy Accelerator, says historically Yandex has tried to resist government demands for data and has proved better than other firms. (In June, it was fined 2 million rubles ($24,000) for not handing data to Russian security services.) However, Shakirov says he thinks things are changing. “I am inclined to believe that Yandex will be attempted to be nationalized and, as a consequence, management and policy will change,” Shakirov says. “And as a consequence, user data will be under much greater threat than it is now.”
Bakunov, the former Yandex engineer, who reviewed some of McCrea’s findings at WIRED’s request, says he is scared by the potential for the misuse of data going forward. He says it looks like Russia is a “new generation” of a “failed state,” highlighting how it may use technology. “Yandex here is the big part of these technologies,” he says. “When we built this company, many years ago, nobody thought that.” The company’s head of privacy, Cherevko, says that within the restructuring process, “control of the company will remain in the hands of management.” And its management makes decisions based on its “core principles.”
But the leaked code shows, in one small instance, that Yandex may already share limited information with one Russian government-linked company. Within Crypta are five “matchers” that sync fingerprinting events with telecoms firms—including the state-backed Rostelecom. McCrea says this indicates that the fingerprinting events could be accessible to parts of the Russian state. “The shocking thing is that it exists,” McCrea says. “There's nothing terribly shocking within it.” (Cherevko says the tool is used for improving the quality of advertising, helping it to improve its accuracy, and also identifying scammers attempting to conduct fraud.)
Overall, McCrea says that whatever happens with the company, there are lessons about collecting too much data and what can happen to it over time when circumstances change. “Nothing stays harmless forever,” she says.
5 notes
·
View notes
Text
10 Web Developer Secrets You Need to Know for Success in 2024

In the fast-paced world of web development, staying ahead of the curve is essential for success. As we venture into 2024, it's crucial to uncover the latest secrets and strategies that can propel your web development endeavors to new heights. Let's delve into ten invaluable insights that every web developer should know for a prosperous year ahead.
Embrace Progressive Web Apps (PWAs)
In 2024, the prominence of Progressive Web Apps (PWAs) continues to soar. These innovative web applications offer users an immersive, app-like experience directly from their browsers. By embracing PWAs, developers can enhance user engagement, improve performance, and seamlessly integrate features like push notifications and offline functionality.
Prioritize Mobile-First Design
With mobile devices dominating internet usage, prioritizing mobile-first design is non-negotiable. Crafting websites with mobile users in mind ensures optimal responsiveness and usability across various devices and screen sizes. Embrace responsive design principles to deliver a seamless browsing experience that caters to the needs of your audience.
Harness the Power of AI and Machine Learning
AI and machine learning technologies are revolutionizing the field of web development. From personalized content recommendations to intelligent chatbots, incorporating AI-driven solutions can elevate user experiences and streamline processes. Explore AI-powered tools and frameworks to unlock new possibilities and stay ahead of the competition.
Optimize for Core Web Vitals
In 2021, Google introduced Core Web Vitals as essential metrics for evaluating user experience. To rank higher in search results and provide users with a smoother browsing experience, prioritize optimizing for Core Web Vitals. Focus on metrics like loading speed, interactivity, and visual stability to ensure your website meets Google's standards and delights visitors.
Implement Voice Search Optimization
The prevalence of voice-enabled devices continues to grow, shaping the way users interact with the web. To capitalize on this trend, implement voice search optimization strategies to make your website more discoverable through voice queries. Consider natural language patterns and long-tail keywords to optimize content for voice search queries effectively.
Enhance Security with HTTPS
Security remains a top priority for web developers, especially in an era marked by increasing cyber threats. Transitioning your website to HTTPS not only encrypts data transmitted between the user's browser and your server but also instills trust and credibility among visitors. Prioritize security protocols to safeguard sensitive information and protect your users' privacy.
Leverage Content Delivery Networks (CDNs)
Content Delivery Networks (CDNs) play a pivotal role in optimizing website performance and reliability. By distributing content across multiple servers worldwide, CDNs reduce latency and ensure faster loading times for users across the globe. Integrate CDNs into your web development workflow to deliver content swiftly and efficiently, regardless of geographical location.
Stay Abreast of Accessibility Standards
Accessibility is an integral aspect of web development, ensuring that websites are inclusive and accessible to all users, regardless of disabilities or impairments. Stay abreast of accessibility standards such as the Web Content Accessibility Guidelines (WCAG) and implement best practices to make your website more usable and navigable for everyone.
Embrace Serverless Architecture
Serverless architecture offers a streamlined approach to web development, eliminating the need to manage servers and infrastructure manually. By leveraging cloud-based services and functions, developers can focus on writing code and delivering value without worrying about scalability or maintenance. Embrace serverless architecture to enhance agility, reduce costs, and accelerate development cycles.
Cultivate Continuous Learning and Adaptation
In the dynamic landscape of web development, continuous learning and adaptation are paramount. Stay curious, explore emerging technologies, and embrace new methodologies to evolve with the industry's ever-changing demands. Cultivate a mindset of lifelong learning, experiment with new tools and techniques, and adapt your skills to thrive in the digital ecosystem.
As we navigate the complexities of web development in 2024, embracing these secrets and strategies can position you for success in an ever-evolving landscape. By staying ahead of trends, prioritizing user experience, and leveraging innovative technologies, you can unlock new opportunities and achieve remarkable feats in the realm of web development.
#web development company#app development#web development services#web development#mobile app development
2 notes
·
View notes
Text
The Importance of Increase Crawling and Indexability
In the ever-evolving landscape of digital marketing and online visibility, the significance of search engine optimization (SEO) cannot be overstated. One crucial aspect of SEO is ensuring that your website's content is effectively crawled and indexed by search engines. In this blog post, we delve into the importance of increased crawling and indexability for your website's success.
Crawling refers to the process by which search engine bots systematically navigate through the vast expanse of the internet, discovering and analyzing web pages. Indexing, on the other hand, involves storing and organizing the information collected during crawling to facilitate quick and relevant search results.
The Importance of Increase Crawling and Indexability
Enhanced Visibility
When search engine bots successfully crawl and index your website, your content becomes visible to users who are actively searching for information related to your industry, products, or services. This visibility is crucial for attracting organic traffic to your website.
Faster Updates
Websites that are easily crawlable and indexable tend to receive quicker updates on search engine results pages (SERPs) when new content is added. This rapid indexing ensures that your latest blog posts, products, or news articles are available to users as soon as possible.
Optimized User Experience
Improved crawling and indexability lead to a better user experience. Users can access relevant information promptly, reducing their search time and increasing their overall satisfaction with your website. This can contribute to higher engagement rates and repeat visits.
Effective Keyword Targeting
When search engines index your content accurately, they can match it with relevant search queries. This means that your website's pages will show up in search results for the keywords and phrases you're targeting, increasing the likelihood of attracting quality traffic.
Mobile Friendliness
With the increasing use of mobile devices for internet browsing, mobile-friendliness has become a key ranking factor for search engines. Websites that are crawlable and indexable on both desktop and mobile platforms have a better chance of ranking higher in mobile search results.
Technical SEO Impact
Effective crawling and indexability are often linked to a well-structured website with clean code, optimized URLs, and proper internal linking. Addressing these technical aspects not only improves indexability but also enhances the overall SEO health of your website.
Competitive Edge
In a competitive online market, any edge you can gain is valuable. A website that is easily crawlable and indexable can outrank competitors who neglect these aspects, leading to increased traffic and potential conversions.
To ensure increased crawling and indexability for your website, consider the following practices
XML Sitemap Submission
Submit XML sitemaps to search engines to guide their crawlers to important pages on your site.
Internal Linking
Properly interlink your website's pages to help search engine bots discover and index content more effectively.
Optimize Robots.txt
Use a robots.txt file to guide crawlers on which parts of your site to crawl and which to exclude.
Page Speed Optimization
Faster-loading pages are more likely to be crawled and indexed efficiently.
Structured Data Markup
Implement structured data to provide search engines with additional context about your content.
In conclusion
the importance of increased crawling and indexability cannot be underestimated in the realm of SEO. A website that is easily discoverable by search engine bots and effectively indexed stands a better chance of attracting organic traffic, enhancing user experiences, and ultimately achieving its online goals. Click here to know more for details.
2 notes
·
View notes
Text
Web5Studio: Elevating Web Design, Web Development, and SEO in Nagpur City
In the ever-evolving digital landscape, having a strong online presence is paramount for businesses of all sizes. With consumers turning to the internet for everything from information to shopping, a well-designed website is the cornerstone of success. In Nagpur City, one company stands out for its excellence in providing top-notch web design, web development, and SEO services - Web5Studio. Renowned for their commitment to delivering innovative and customer-centric solutions, Web5Studio has earned a reputation as a leading web services provider in the region.

Understanding Web5Studio:
Web5Studio is a dynamic web services company based in Nagpur City. With a team of highly skilled professionals, the company specializes in offering a comprehensive range of services that include web design, web development, and search engine optimization (SEO). Since its inception, Web5Studio has been committed to helping businesses establish a strong digital presence and boost their online visibility, thereby enhancing their overall growth and success.
Web Design Services:
A well-designed website is the virtual storefront of any business, making a lasting impression on visitors. Web5Studio excels in crafting visually appealing, intuitive, and user-friendly websites that captivate audiences and ensure a seamless browsing experience. Understanding the significance of responsive design, their websites adapt effortlessly to various devices, ensuring accessibility for users on desktops, laptops, tablets, and smart phones.
Web5Studio's design process involves thorough collaboration with clients, understanding their unique requirements, brand identity, and target audience. By combining creativity with functionality, they create bespoke designs that reflect the essence of the business, instilling trust and credibility among site visitors.
Web Development Solutions:
Web5Studio's web development services are built on a foundation of cutting-edge technologies and coding practices. Their expert development team possesses a wealth of experience in various programming languages and frameworks, enabling them to create robust, scalable, and secure websites.
Whether it's an informational website, e-commerce platform, or a complex web application, Web5Studio excels in tailoring solutions to suit individual business needs. Their commitment to delivering timely projects without compromising on quality has earned them accolades from numerous satisfied clients.
SEO Excellence:
In today's highly competitive digital landscape, mere existence on the internet is not enough. Visibility is key, and that's where SEO comes into play. Web5Studio takes pride in its result-driven SEO strategies that aim to enhance a website's organic search rankings.
By conducting in-depth keyword research, optimizing website content, refining meta tags, and building high-quality backlinks, Web5Studio improves a website's visibility on search engine results pages. The team stays up-to-date with the latest SEO trends and algorithms, ensuring their clients' websites maintain a competitive edge in the online realm.
Customer-Centric Approach:
One of the factors that set Web5Studio apart from its competitors is its customer-centric approach. Every project is treated with utmost importance, and clients are kept involved throughout the development process. Regular communication and feedback loops ensure that the final product aligns with the clients' expectations.
Moreover, Web5Studio provides excellent post-launch support and maintenance services, making them a reliable long-term partner for businesses seeking sustained growth in the digital world.
Name:- Web5Studio
Address:- Plot No. 58/B Rameshwari Ring Road, Near Hatagade Kirana Stores, Hawarapeth Parvati Nagar, Nagpur Maharastra 440027.
Contact No:- +917709508692
Website:- https://www.web5studio.com
Conclusion:
Web5Studio has become a shining star in the Nagpur City web services scene due to its commitment to excellence, creativity, and customer satisfaction. Their proficiency in web design, web development, and SEO services has enabled numerous businesses to thrive in the competitive online landscape. As the digital world continues to evolve, Web5Studio stands tall as a trusted ally for businesses aspiring to make a mark in the virtual realm.
#Web5Studio#WebDesign#WebDevelopment#SEO#DigitalServices#NagpurCity#OnlinePresence#WebsiteDesign#ResponsiveDesign#WebsiteDevelopment#SEOServices#BusinessGrowth#CustomerSatisfaction#DigitalMarketing#EcommerceSolutions#WebServicesNagpur#OnlineBusiness#SEOStrategy#WebDesignNagpur#WebDevelopmentNagpur
3 notes
·
View notes
Text
Vanitywagon Promo Code (AVA) – Save ₹300 on Clean Beauty Combos | Vanitywagon Discount Code Bonus

If you're someone who values clean, cruelty-free, and sustainable beauty products, Vanitywagon is probably already on your radar. This Indian beauty platform is known for offering a curated selection of toxin-free skincare, haircare, makeup, and wellness brands. Whether you’re a seasoned clean beauty enthusiast or just starting to transition away from conventional cosmetics, Vanitywagon makes it easier—and more affordable—to shop consciously.
With their latest Vanitywagon Promo Code (AVA), customers can now save ₹300 on specially curated clean beauty combos. These combos bundle your favorite essentials into a cost-effective package, and with the added discount from the AVA code, it’s a deal too good to miss.
To unlock the offer immediately, simply visit this Vanitywagon Discount Code (AVA) page and apply the code during checkout.
What Makes Vanitywagon Special?
Vanitywagon is not just an online store—it’s a movement toward transparency and safety in beauty. The platform only lists products that are free from harmful chemicals such as parabens, sulfates, phthalates, and artificial fragrances. They also prioritize cruelty-free, vegan, and eco-conscious brands, making them a reliable choice for consumers looking to make mindful purchases.
By offering everything from face cleansers and sunscreens to lipsticks and bath essentials, Vanitywagon caters to a wide range of beauty and personal care needs—all in one place.
The biggest bonus? You can now enjoy additional savings with the Vanitywagon Promo Code (AVA).
How to Use the AVA Code to Save ₹300
Getting your ₹300 discount is quick and easy:
Visit the Vanitywagon website.
Browse through the “Combos” section or pick any bundled offers eligible for promo codes.
Add your selected clean beauty combo(s) to your cart.
At checkout, enter the Vanitywagon Promo Code (AVA).
Instantly receive ₹300 off your total.
This offer is perfect for those looking to try a full routine from one brand or mix-and-match products across categories—all while saving money.
Why Buy Combos on Vanitywagon?
Combos are already a great way to save, as they typically come with built-in discounts. They’re also thoughtfully designed to work together, whether it’s a skincare set with cleanser, toner, and moisturizer or a haircare pack with shampoo, conditioner, and hair serum.
Here’s why buying combos makes sense:
Better value per product
Curated combinations that target specific concerns
One-stop solution for complete care
Eligible for extra discounts like the AVA code
When you apply the Vanitywagon Promo Code (AVA), you amplify your savings—bringing both value and quality to your beauty routine.
Brands You Can Trust
Vanitywagon partners with some of the most respected clean beauty brands in India. This includes names like:
Juicy Chemistry
Earth Rhythm
Neemli Naturals
Disguise Cosmetics
Daughter Earth
Aqualogica
Each of these brands adheres to high standards of purity, sustainability, and effectiveness. You can build a full regimen from one brand or mix across different ones—either way, your skin will thank you.
The best part? Most of these brands offer combo packs that are eligible for the ₹300 discount using the Vanitywagon Promo Code (AVA).
Referral Bonus for Long-Term Savings
Aside from one-time savings, Vanitywagon offers a smart way to continue earning discounts through their referral program. After your first purchase using a code like AVA, you’ll receive your own referral link. Share it with friends and family—and whenever someone shops using your code, you both benefit.
Referral bonuses are typically credited as wallet balance or discount vouchers, which you can redeem on future purchases.
So, once you’ve unlocked the Vanitywagon Promo Code (AVA) savings, don’t forget to pass the good vibes forward and earn along the way.
Ideal Time to Use the AVA Code
The AVA promo code is especially useful during:
Seasonal combo launches
Festive sales
Sitewide offers where codes are stackable
When restocking your skincare or haircare essentials
Combining a limited-time deal with the guaranteed ₹300 discount gives you the upper hand on pricing—while still prioritizing clean and safe ingredients.
Tips for Smart Shopping
Here are a few quick tips to get the most from your Vanitywagon experience:
Compare combo kits across brands to find the best match for your skin type and needs.
Watch out for limited-edition boxes, which often contain more value than regular kits.
Use the AVA code even on discounted combos, as many allow stacking.
Subscribe to the newsletter to get notified of flash deals and code extensions.
Refer and repeat—build your referral credits for future savings.
Why the Vanitywagon Promo Code (AVA) is a Must-Have
While Vanitywagon offers several promo codes throughout the year, the AVA code is consistently among the most generous. A flat ₹300 off on bundles that are already priced lower than MRP is a double win.
What sets this code apart:
Works on curated combos, not just individual items.
No complex rules or cart limits.
Valid across a wide range of product types and brands.
Can be used by both new and existing customers.
Whether you’re gifting someone or revamping your own beauty shelf, the Vanitywagon Promo Code (AVA) ensures you’re getting the most value out of every order.
Conclusion
Shopping clean doesn’t have to be costly. With platforms like Vanitywagon and special offers such as the Vanitywagon Promo Code (AVA), switching to toxin-free, cruelty-free beauty becomes simple and affordable. Take advantage of the ₹300 discount on beauty combos today and experience the power of ethical skincare and cosmetics without breaking the bank.
Remember—great skin, great savings, and great choices all start with the right code. Begin your journey with the Vanitywagon Promo Code (AVA) and make clean beauty a habit, not a luxury.
0 notes
Text
Website Developer in Dubai: Crafting Digital Excellence
Dubai is a global hub for business, innovation, and technology, making it essential for companies to have a strong online presence. A Website Developer In Dubai plays a crucial role in helping businesses establish their digital footprint with custom, responsive, and high-performing websites. Whether you're a startup, SME, or large enterprise, hiring a skilled web developer can significantly impact your brand’s visibility, user engagement, and overall success.

Why Hire a Professional Website Developer in Dubai?
1. Customized Web Solutions
A professional website developer in Dubai doesn’t just create a basic website; they design a tailored solution that aligns with your business goals. From e-commerce platforms to corporate websites and dynamic web applications, developers use the latest technologies to ensure your site stands out in a competitive market.
2. Responsive and Mobile-Friendly Designs
With a majority of users browsing on mobile devices, having a responsive website is non-negotiable. A skilled web developer in Dubai ensures your site adapts seamlessly across all devices, improving user experience and boosting search engine rankings.
3. SEO Optimization
A well-designed website is useless if it doesn’t rank on search engines. Experienced developers integrate SEO best practices during the development phase, ensuring faster load times, clean code, and proper meta tags—key factors that help your site rank higher on Google.
4. Enhanced Security Features
Cybersecurity is a major concern for businesses in Dubai. Professional developers implement robust security measures, including SSL certificates, secure payment gateways, and regular updates, to protect your website from cyber threats.
5. Ongoing Support and Maintenance
A website developer in Dubai doesn’t just build your site and leave; they provide ongoing maintenance, updates, and technical support to ensure smooth functionality and performance.
Choosing the Right Website Developer in Dubai
When selecting a web developer in Dubai, consider the following:
Portfolio & Experience – Review their past projects to assess their expertise.
Technology Stack – Ensure they use modern frameworks like React, Angular, or WordPress.
Client Reviews – Check testimonials to gauge reliability and customer satisfaction.
Post-Launch Support – Confirm if they offer maintenance and updates.
Conclusion
A well-developed website is the foundation of a successful online business. By hiring a professional website developer in Dubai, you ensure a high-quality, secure, and SEO-optimized site that drives traffic and conversions. Whether you need an e-commerce platform, a corporate website, or a custom web application, investing in expert development services will give your business a competitive edge in Dubai’s digital landscape.
0 notes
Text
You may have seen me post about this on my Instagram story, but I just had to share a link here. From the creator:
“This short is adapted primarily from The Wild Party, 1929, Dir. Dorothy Arzner, a lesbian and one of the only women directors in the early decades of Hollywood. While browsing the archive for material of the era, I was inspired by the relatively subversive pre-code portrayals of women's sexuality, and wanted to overlay that with a contemporary romantic construct as well as celebrate the inherent gay subtext of the original film.
Arzner was crucial in the development of the cinematic medium, she even invented the boom mic while filming The Wild Party! Arzner frequently collaborated with the star of this short, the iconic Clara Bow. You may have noticed Bow’s reemergence into the cultural lexicon in 2024 upon being invoked on the latest album from pop titan Taylor Swift. Bow famously inspired the origins of the term "It Girl", reaching archetypal status for her bold personality and authenticity.”
0 notes
Text
Transport Layer Security (TLS): The Backbone of a Secure Internet
In today’s digitally connected world, security and privacy are more important than ever. Whether you're accessing your bank account, shopping online, or simply browsing a website, you're likely using Transport Layer Security (TLS) — the cryptographic protocol that protects internet communications.
In this post, we’ll explore:
What TLS is and why it matters
How TLS works under the hood
TLS vs SSL
Real-world use cases
Common threats and how TLS mitigates them
Transport Layer Security (TLS) is a cryptographic protocol that ensures privacy, integrity, and authenticity of data exchanged over a network. It’s widely used to secure:
Web traffic (HTTPS)
Email (SMTP, IMAP, POP)
Messaging (XMPP, SIP)
VPNs and more
TLS operates between the transport layer (e.g., TCP) and the application layer (e.g., HTTP), encrypting the data before it's transmitted over the internet.
How TLS Works: Step by Step
When a client (e.g., browser) connects to a server over HTTPS, here's what happens:
1. Handshake Initiation
The client sends a ClientHello message:
Supported TLS versions
List of supported cipher suites
Random number (used in key generation)
Optional: SNI (Server Name Indication)
2. Server Response
The server replies with a ServerHello message:
Selected cipher suite
TLS version
Server's digital certificate (usually an X.509 certificate)
Optional: server key exchange
3. Authentication & Key Exchange
The client verifies the server's certificate via a trusted Certificate Authority (CA).
Both parties generate or agree on session keys using techniques like Diffie-Hellman or RSA.
4. Session Key Generation
Once keys are exchanged:
Both client and server compute a shared symmetric session key.
5. Secure Communication
All subsequent data is:
Encrypted using the session key
Authenticated (to detect tampering)
Integrity-protected using MACs (Message Authentication Codes)
TLS vs SSL: What’s the Difference?
People often say “SSL” when they mean TLS. Here’s the truth:Feature SSL (Deprecated)TLS (Current)Latest VersionSSL 3.0 (1996)TLS 1.3 (2018)SecurityVulnerableStrongUse TodayNone (shouldn't be used)Everywhere
Modern websites and applications use TLS 1.2 or TLS 1.3, and all versions of SSL are considered insecure.
TLS Use Cases
HTTPS (TLS over HTTP)
Secure browsing (padlock in browser)
Required for PCI DSS, GDPR compliance
Email Encryption
Secure SMTP (STARTTLS)
IMAP/POP with TLS
VoIP and Messaging
TLS protects SIP, XMPP, and chat services
VPNs
OpenVPN uses TLS for secure tunnels
APIs and Microservices
Internal and external APIs often rely on TLS to secure REST and GraphQL endpoints
Common Threats and TLS ProtectionsThreatTLS DefenseMan-in-the-Middle (MITM)Authentication via certificatesEavesdroppingSymmetric encryption of session dataTampering or Data CorruptionMessage integrity with MACsReplay AttacksRandom values and sequence numbersDowngrade AttacksTLS version enforcement & SCSV mechanism
Best Practices for TLS Configuration
Use TLS 1.2 or TLS 1.3 only.
Disable SSL and TLS 1.0/1.1 completely.
Use strong cipher suites (e.g., AES-GCM, ChaCha20).
Regularly renew and monitor your TLS certificates.
Enable HSTS (HTTP Strict Transport Security).
Use tools like SSL Labs, Mozilla Observatory to test your server.
TLS in Action (Example)
When you visit https://sfouresolutions.com:
Your browser initiates a TLS handshake.
The server sends its certificate.
A session key is negotiated.
Your browser encrypts the HTTP request with that key.
The server decrypts it, processes it, and responds securely.
All of this happens within milliseconds, seamlessly.
Final Thoughts
TLS is a foundational technology that quietly protects the internet. As cyber threats grow in sophistication, strong TLS configurations and practices are not optional — they are essential.
Whether you're a developer, sysadmin, or business owner, understanding TLS helps you build safer systems and protect user trust.
0 notes
Text
Elevate Your Wardrobe: Fashion for Men and Women That Defines Your Style
In a world where trends shift by the minute, staying ahead in fashion for men and women isn't just about following the crowd—it’s about owning your look with confidence. Whether you're revamping your seasonal wardrobe or shopping for standout pieces, there's one thing every fashion-forward individual looks for: good quality clothes that not only look great but also last.
At JustYourOutfit, fashion isn't just about garments—it's about self-expression, individuality, and affordability. This UK-based online clothing store delivers on every front, offering on-trend apparel for both men and women, all at prices that won't break the bank.
Discover Trendy Fashion for Men and Women

From oversized hoodies and cargo trousers for men to slinky dresses and co-ord sets for women, JustYourOutfit offers a curated selection that reflects the current pulse of fashion. Whether you're going casual, bold, or streetwear-inspired, there's something that aligns with every mood and occasion.
Men can find wardrobe essentials like:
Printed shirts, bomber jackets, and track sets
Sleek outerwear and minimalist staples
Women will love:
Crop tops, ruched bodycon dresses, and matching sets
Versatile pieces perfect for brunches, holidays, or stay-at-home lounging
New styles drop every week, making it easy to refresh your look with the latest seasonal trends.
Why Buy Good Quality Clothes Online from JustYourOutfit?
In today’s fast-paced digital world, it’s more important than ever to buy good quality clothes online from a source you can trust. JustYourOutfit focuses on combining style and durability, ensuring that every item feels as good as it looks.
Here’s why shoppers keep coming back:
Premium fabrics that last through every wear and wash
Affordable pricing without compromising on quality
Pre-order options that allow you to secure your favorite styles early
Sustainable shopping that reduces waste by producing what’s in demand
With options for all body types and fashion preferences, shopping online becomes not only convenient but also inspiring.
Seamless Shopping, Fast Delivery
JustYourOutfit makes the online shopping experience hassle-free. With UK next-day delivery options available (when you order by 11 PM), you'll never have to wait long to wear your favorite picks. Multiple delivery methods—including Saturday and saver delivery—give you flexibility and control over your order.
Plus, the website’s clear filters and easy-to-navigate design make it simple to browse by category, size, color, and price.
Join the JustYourOutfit Fashion Movement
Fashion is more than clothing—it's a community. JustYourOutfit stays connected with its fans and trendsetters across platforms. Want outfit inspo, sneak peeks, and giveaways? Follow them on:
Facebook
Youtube
Twitter
Instagram
Whether you're styling a date night look or searching for a streetwear statement piece, these channels offer a constant stream of style inspiration.
Final Thoughts
Staying fashionable doesn’t have to be stressful or expensive. With JustYourOutfit, you get access to trend-led fashion for men and women and the assurance that when you buy good quality clothes online, you're making a smart, stylish investment.

So go ahead—refresh your wardrobe, explore something bold, and embrace your next outfit obsession. Your style story starts here.
Shop now at JustYourOutfit and use code SUM11 for an exclusive discount!
1 note
·
View note